How to Upload a Verse Shell Script Htb Challenge With Splunk
Splunk [Part-1]— Try Hack me Room

What is Splunk?
Splunk is a software tool for searching, analyzing and visualizing machine-generated data obtained from the websites, apps, sensors, computers, etc. that brand up the company and The infrastructure.
For an organisation, Splunk provides plenty of opportunities. Any of the advantages of using Splunk are Offers improved GUI in a dashboard with real-time visibility Past delivering quick results, it reduces troubleshooting and solving fourth dimension. It is a technique that is ideally used for root cause analysis. You lot tin create graphs, warnings, and dashboards with Splunk.
Using Splunk, you tin speedily check and investigate detail findings. It helps you to troubleshoot any malfunction scenario for enhanced results. Helps you rails and make an educated decision on some market indicators Splunk allows Artificial Intelligence to be integrated into the information plan. Enables you to obtain valuable Tactical Information from your computer data
Task 2 →Can you dig it?
Splunk queries always brainstorm with this command implicitly unless otherwise specified. What command is this? When performing additional queries to refine received data this control must be added at the start. This is a prime example of a slight pull a fast one on question.
search
When searching for values, information technology's adequately typical within security to look for uncommon events. What control tin we include within our search to find these?
rare
What about the inverse? What if nosotros want the well-nigh common security event?
top
When we import information into splunk, what is information technology stored under?
index
We tin can create 'views' that permit united states of america to consistently pull up the aforementioned search over and over again; what are these called?
dashboard
Importing data doesn't always get as planned and nosotros can sometimes finish upward with multiple copies of the same data, what control do we include in our search to remove these copies?
dedup
Splunk tin be used for more but a SIEM and it's commonly used in marketing to track things such as how long a shopping trip on a website lasts from start to finish. What command tin we include in our search to track how long these event pairs take?
transaction
In a manner similar to Linux, we can 'pipe' search results into further commands, what character do nosotros utilize for this?
|
In performing data analytics with Splunk (ironically what the tool is at information technology'southward core) it's useful to rails occurrences of events over time, what command do we include to plot this?
timechart
What about if we want to gather general statistical data about a search?
stats
Data imported into Splunk is categorized into columns called what?
fields
When we import information into Splunk we tin can view it's point of origination, what is this called? I'm looking for the machine aspect of this here.
host
When we import data into Splunk we can view its bespeak of origination from within a organisation, what is this called?
source
Nosotros tin classify these points of origination and grouping them all together, viewing them every bit their specific type. What is this called? Use the syntax institute within the search query rather than the proper name for this.
sourcetype
When performing functions on data nosotros are searching through nosotros use a specific command prior to the evaluation itself, what is this command?
eval
Dear it or hate it regular expression is a massive component to Splunk, what command exercise we use to specific regex within a search?
male monarch
It'due south adequately common to create subsets and specific views for less technical Splunk users, what are these chosen?
pivot table
What is the proper name of the time date field in Splunk
_time
How practice I specifically include but the first few values found inside my search?
caput
More useful than you would otherwise imagine, how do I flip the order that results are returned in?
reverse
When viewing search results, it'due south often useful to rename fields using user-provided tables of values. What command do nosotros include within a search to practise this?
lookup
Nosotros tin collect events into specific time frames to exist used in further processing. What control practice we include within a search to practice just that?
bucket
We can besides ascertain data into specific sections of time to be used within chart commands, what command do nosotros employ to fix these lengths of time? This is dissimilar from the previous question equally we are no longer collecting for further processing.
bridge
When producing statistics regarding a search it'south common to number the occurrences of an event, what control practice we include to exercise this?
count
Last merely not least, what is the website where you can find the Splunk apps at?
Splunkbase.splunk.com
We can likewise add new features into Splunk, what are these called?
Apps
What does SOC correspond?
Security operations eye
What does SIEM represent?
Security information and event management
How about BOTS?
Boss of the soc
And CIM?
Common information model
what is the website where yous can notice the Splunk forums at?
Answers.splunk.com
Task 5 →Advanced Persistent Threat

What IP is scanning our spider web server?

To get the IP first we need to go to the reconnaissance tab like paradigm-one

Then click Finding the IP Scanning your web server(part1 , part 2)
And so it will lead to another tab with default search query "alphabetize=botsv1 imreallynotbatman.com" similar this we demand to build all the other query one tiptop of this.

index=botsv1 imreallynotbatman.com
| stats count by source
| sort -count
| caput x index=botsv1 imreallynotbatman.com
| stats count by source → (calculate the summary of source by counting )
| sort -count → (sort the source count in to a descending lodge )
| head 10 →(take the get-go 10 results )
Now in result you lot tin see in that location is a source file call stream:http this is the identify that all http requests are stored
At present lets find out what are the scr_ip's that did http requests to our site.

index = botsv1 imreallynotbatman.com sourcetype = stream:http
|stats count past src_ip
|sort -count answer is 40.80.148.42
What web scanner scanned the server?
index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.lxxx.148.42"
|stats count by src_headers
|sort -count
|head v index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42"
|stats count by src_headers →(src_headers are the header files of HTTP requests)
|sort -count
|head five

Answer is Acunetix
What is the IP address of our spider web server?
index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42"
| stats count by dest_ip
| sort -count 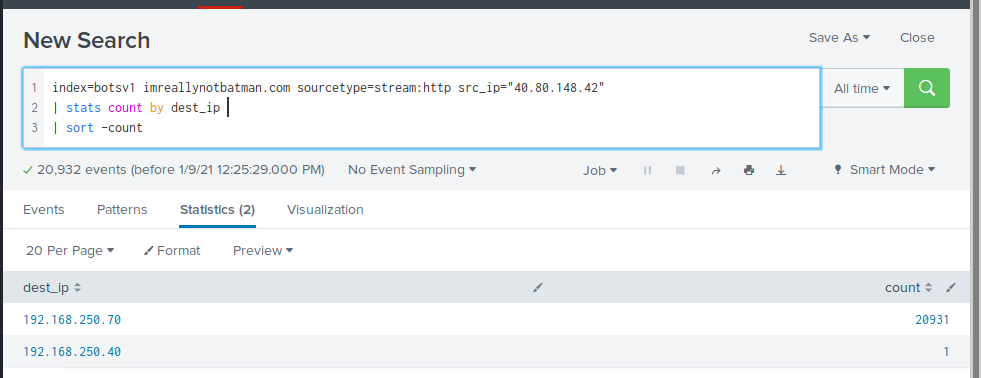
IP →192.168.250.70
What content management organisation is imreallynotbatman.com using?
index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="forty.80.148.42"
| stats count by uri
| sort -count
| head 10 
answer is Joomla
What address is performing the creature-forcing assail against our website?
Most of the brute force requests must be Get or Post methods and then now lets count how many post and go request nosotros got for this site
index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.fourscore.148.42"
| stats count by http_method
| sort -count 
So in here you lot can come across Most of the requests are postal service requests in that location for assail besides happened this manner. We know for creature strength assault we need to have username and countersign variables
now lets have one variable equally username and search 1 asking to get the other variables lets run this command
index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" http_method="POST" username
| tabular array dest_content
| head 1 So now we can see countersign variable proper noun is passwd

Now lets notice out how many Login request we got in hither
this is the command we gonna use
index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="Mail" form_data=*username*passwd*
| stats count by src_ip 

now you can see ii IP address and 23.22.63.114 IP did the brute forcefulness assail confronting our site
then the answer is 23.22.63.114
What was the first password attempted in the assail?
This search command is trivial chip similar to the previous command
index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd*
| rex field=form_data "username=(?<u>\w+)"
| rex field=form_data "passwd=(?<p>\westward+)"
| tabular array _time, u, p
| sort by _time
| caput 3 I will break downwardly the command for you information technology is easy to sympathise..
Use the rex command to either extract fields using a standard expression called classes.
use ( *, +, ? ) to ascertain how to match the groups to the literal pattern. For example, * matches 0 or more, + matches 1 or more, and ? matches 0 or 1.
rex field=form_data "username=(?<u>\w+) Rex — extract , field=from_data username=(? <u>\w+) →select the username column and stand for as U and Find one or more than alphanumeric characters in username
table _time, u, p
| sort by _time
| head three create tabular array with 3 column name _time, u and p and sort past _time and print first iii result
in here I took the showtime three results.

So the First password is 12345678
One of the passwords in the brute forcefulness attack is James Brodsky'south favorite Coldplay song. Which vi character song is it?
In this question they saying something about Coldplay vocal for that we need to take the all the Coldplay song list. you can re-create that from here and need to save it every bit a csv format.
Now in Splunk, go to Settings > Lookups > Lookup tabular array files > New lookup Table File.

If you didn't get the respond run the control

To cheque whether your file is uploaded correctly
I am stopping from here this blog is kind of long with in this calendar week I will try to upload the 2nd office of the Splunk..
Till then see youu…!!! Stay safety , stay curious
Source: https://mohomedarfath.medium.com/splunk-part-1-try-hack-me-room-969a59b0a5e2
0 Response to "How to Upload a Verse Shell Script Htb Challenge With Splunk"
Post a Comment